Distributed Denial of Services (DDoS) attacks can take any website offline. Even Google and GitHub, with their immense resources, struggle to stay online during a large attack. Even worse, anyone with a few dollars can launch one.
If you host websites, you and your users could be hit with a denial of service attack big enough to take sites down for hours or even days. However, the worst effects of DDoS attacks can be avoided with the right tools, which is why cPanel & WHM includes several DDoS mitigation features.
In this article, we explain what denial of service attacks are, how they work, and what you can do to survive them.
What Is a DDoS Attack and How Does It Work?
Before we get to Distributed Denial of Service attacks, let’s look at how a plain old Denial of Service (DoS) attack works.
Denial of Service Attacks
A Denial of Service (DoS) attack is an attempt to overwhelm servers with malicious requests and connections. A server’s primary purpose is to accept and process network connections. Each one consumes a chunk of bandwidth, memory, and processing power, and too many can use up all of the available resources, preventing new connections. When that happens, websites can’t be accessed; they are, in effect, knocked off the internet.
Attackers exploit this vulnerability by creating so many connections and sending so much data that the server or network interface can’t cope. You might be wondering why admins don’t simply block hostile connections. That’s what’s so sneaky about DoS attacks: how do we tell good connections from bad connections when they all look the same?
One way is the source IP address. If an IP address threatens to overwhelm a server, we can block it and move on with our day. Attackers know this, and it’s one of the motivations for Distributed Denial of Service attacks.
Distributed Denial of Service Attacks
In a DDoS attack, the attacker uses a botnet of compromised machines, which can be anything from other servers to consumer laptops to network-connected security cameras. A botnet contains thousands of nodes the attacker can remotely instruct to inundate the target. Because there are so many bots, it’s tough to block them all.
Amplification Attacks
DDoS attacks can get even more devious. Attackers struggle to build botnets that generate enough data to take down a well-prepared hosting provider. Instead of attacking the target directly, they look for an online service to amplify their requests.
When you request a web page, you send a small amount of data, and the server sends back a much larger response. The same is true of some DNS servers, Network Time Protocol (NTP) servers, databases and caches, and others.
For example, the attacker can use their botnet to send requests to an open NTP server. The initial request is tiny, a few bytes. However, the response may be up to 200 times bigger. An attacker who sends a megabyte can generate 200 megabytes of responses. If they spoof the initial request’s IP address, the data goes not to the botnet, but to the target.
This type of amplification is behind some of the most significant DDoS attacks in history, including last year’s 1.35 Terabyte per second attack against GitHub.
What Are the Types DDoS Attacks?
The most popular way to categorize DDoS attacks is according to the part of a network connection they target. You can think of connections as layers of protocols and data formats, with each layer depending on the one below it. For example, the web’s HTTP depends on the lower-level TCP protocol.
Why does this matter? Because the techniques used to mitigate DDoS attacks depend on the network layer they target.
The popular Open Systems Interconnection model (OSI) divides connections into seven layers.
- Layer 1 – the physical layer that transmits raw data over the network’s hardware.
- Layer 2 – the datalink layer, which determines the data’s format.
- Layer 3 – the network layer, which decides which route data takes.
- Layer 4 – the transport layer, which is the level of the TCP and UDP transmission protocols.
- Layer 5 – the session layer, which manages connections and sessions.
- Layer 6 – the presentation layer, which handles data formats and encryption.
- Layer 7 – the application layer, which is the layer we interact with when we click on links or communicate with web applications.
DDoS attacks are typically attributed to one of these layers. A Layer 7 attack targets the application layer, which includes web applications, web servers, and the NTP amplification attack we looked at earlier. Layer 6 attacks often focus on SSL connections. The popular SYN flood attack targets Layer 4, the transport layer, exploiting a weakness in the TCP protocol.
How to Protect Yourself From an Attack
As a server administrator, there is nothing you can do to prevent attackers from sending harmful network requests. However, you can configure both your server’s firewall and webserver to drop requests from misbehaving IP addresses.
To help you protect users from denial of service attacks, cPanel & WHM includes several DDoS mitigation tools.
Config Server Security & Firewall
cPanel & WHM supports the Config Server Security (CSF) firewall, which provides a WHM plugin with a comprehensive configuration interface. First, you will need to follow these instructions to install the plugin.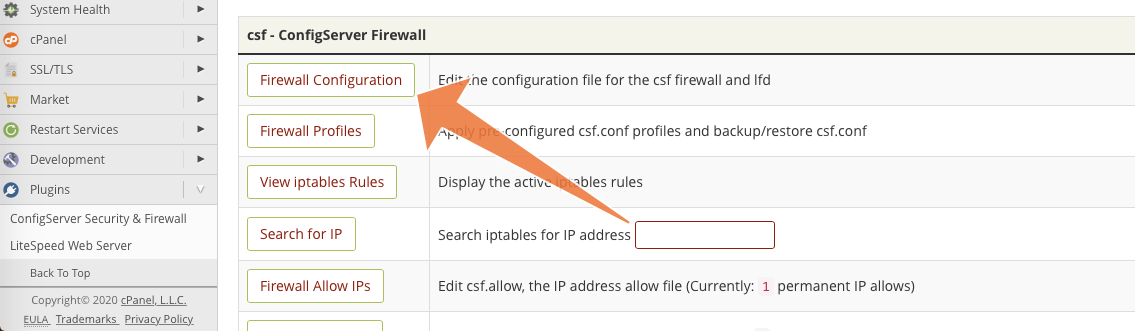
Next, navigate to the ConfigServer Security & Firewall page in the Plugins section of the WHM sidebar menu. Scroll down and click on Firewall Configuration.
Our goal is to turn on Connection Tracking and configure the “CT_LIMIT” value, which controls how many connections the firewall allows from an IP address. During a DDoS attack, a huge number of connections may be made from the same IP, and limiting connections can help to weed out unwanted traffic.
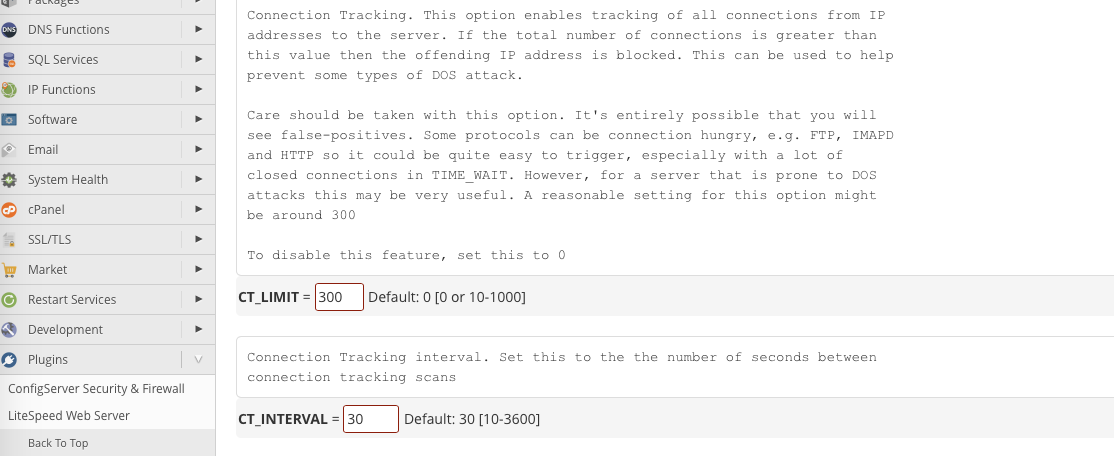
The correct value depends on the nature of the attack and typical traffic patterns, and you may want to experiment, but 300 is a reasonable initial value. Setting this value too low may cause legitimate connections to be dropped.
You may also want to adjust the PORTFLOOD value on the same page. PORTFLOOD limits connections to a particular port. For example, if a server experiences an attack against port 80, the HTTP port, the following limits new connections to 50 within ten seconds, blocking subsequent attempts.
PORTFLOOD = “80;tcp;50;10”
Take a look at the CSF readme file to learn more about the PORTFLOOD syntax.
Finally, one of the most common and easy-to-implement denial of service attacks is the Layer 4 Syn Flood. CSF includes SYN flood protection, which you can turn on in the Port Flood Settings section of the configuration page.
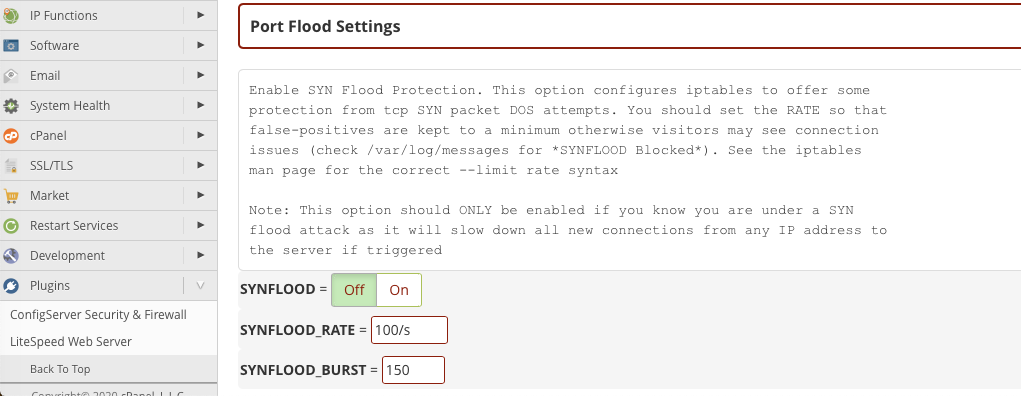
Activate SYN Flood protection and adjust the SYNFLOOD_RATE and SYNFLOOD_BURST settings. The default may be too high to mitigate an ongoing attack. The correct values depend on the specifics of the attack, but 75/s and 50 are a good starting point. Be aware that if you set these values too low, legitimate traffic may face connection problems.
Syn Flood protection should only be turned on during an attack, as it can introduce significant network latency.
Mod_Evasive
Mod_evasive is an Apache module with sophisticated Layer 7 DDoS mitigation features. It detects potential attacks against web applications and takes evasive action by rate-limiting IP addresses that make too many requests in a short time.
First, we need to install the mod_evasive module. Navigate to Easy Apache 4 in WHM’s Software menu. Select the Apache Modules tab, search for “mod_evasive,” and flip the install switch.
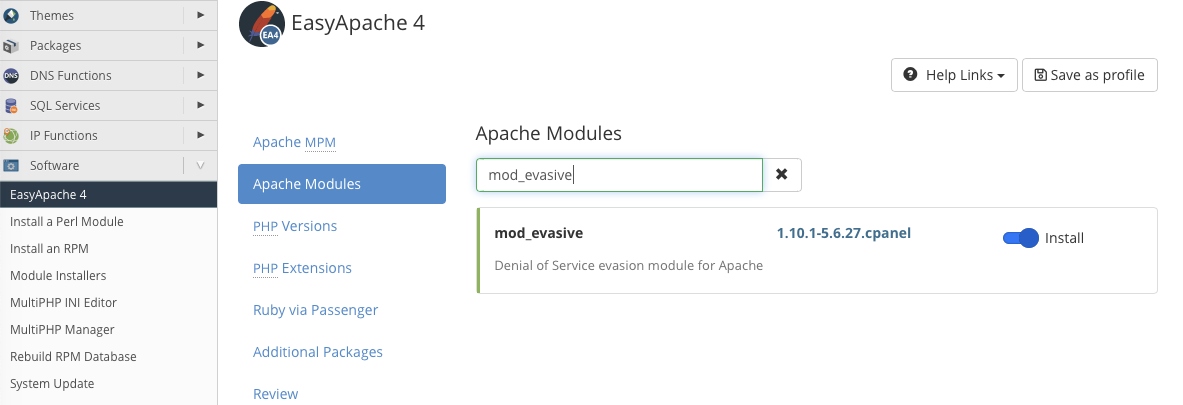
Next, select the Review Tab, scroll to the bottom of the page, and click Provision. WHM may take a few seconds to install the module and its dependencies.
The module has sensible defaults, but you may want to tweak the configuration file, which you will find on the server’s filesystem at:
/etc/apache2/conf.d/300-mod_evasive.conf
If you would like mod_evasive to send an email when it blocks an IP, set an email address in the DOSEmailNotify section. You may need to remove the comment symbol (#) from the beginning of the line.
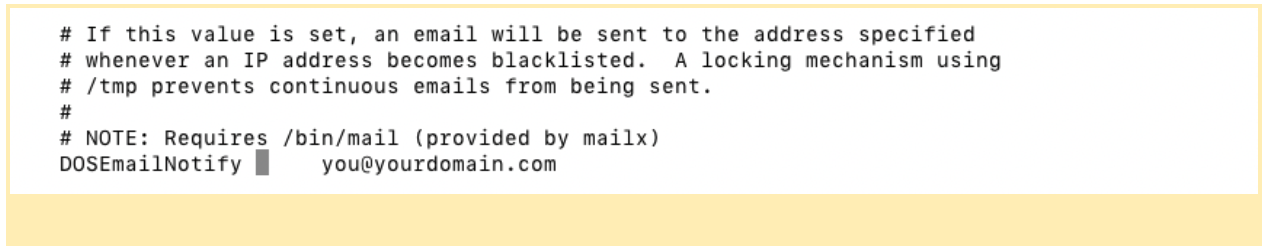
The configuration file is documented with extensive comments, and you can learn more from our mod_evasive documentation.
The cPanel IP Blocker
cPanel includes an IP Blocker that can be used to block both individual addresses and ranges. For a big distributed attack, manual IP blocking is not practical, but it may be useful for smaller attacks. You will find IP Blocker in cPanel’s security menu.
DDoS attacks are a fact of life for web hosting providers. Over time, they have become bigger and easier to carry out. The number of attacks doubled between 2018 and 2019, and we can expect that trend to continue for as long as there is money to be made from threatening the livelihoods of legitimate web hosts and site owners. Fortunately, with cPanel & WHM and a little preparation, you can fight back and keep your users safe.
As always, if you have any feedback or comments, please let us know. We are here to help in the best ways we can. You’ll find us on Seohost's robot portal.